
The Center for Internet Security (CIS) is a U.S.-based, independent nonprofit organization founded in 2000, dedicated to improving cybersecurity for public and private organizations.
CIS builds confidence in the connected world by offering globally recognized cybersecurity best practices. These include the Center for Internet Security Benchmarks and the CIS Critical Security Controls. These tools help people, businesses, and governments protect themselves from widespread cyber threats.
Center for Internet Security is headquartered in East Greenbush, New York. It leads a global IT community to create standards and tools that defend against emerging risks. Its mission is clear: make cybersecurity practical and accessible for everyone, not a luxury for only those with big budgets.
“Cybersecurity should be practical, accessible, and achievable for everyone – not a luxury reserved for the few.” – Tony Sager, CIS Senior VP.
CIS is best known for its Critical Security Controls and Benchmarks. These are adopted by thousands of organizations worldwide to improve their security posture. From Miami, Florida to global tech hubs, companies and government agencies rely on these frameworks. They serve as blueprints for defending against cyber attacks.
This article explains what Center for Internet Security is and explores its core offerings. We’ll cover the CIS Controls, CIS Benchmarks, CIS SecureSuite, and the Community Defense Model. You’ll learn how these tools help organizations achieve secure configurations and improve cyber defenses. We’ll also show how businesses can implement these best practices. Plus, we’ll highlight how a local partner like Ciegate Technologies can support this process.
What is the Center for Internet Security (CIS)?
The Center for Internet Security (CIS) is a nonprofit 501(c)(3) organization. It focuses on improving cybersecurity across both the public and private sectors.
CIS was formed in October 2000 by experts from government, academia, and industry. The goal was to respond to the growing wave of cyber threats through actionable security practices.
Its founding principle is simple: security should be community-driven and accessible to all organizations. That includes those with limited budgets or technical expertise.
The mission of CIS is “to make the connected world a safer place.” It does this by developing and promoting best practices to stop common cyber attacks.
CIS’s two main tools are the CIS Controls and the CIS Benchmarks. These are based on input from global cybersecurity experts. They offer clear, prioritized guidelines any organization can follow to strengthen their systems.
CIS is vendor-agnostic and nonpartisan. It works with a worldwide IT community to ensure its guidance stays current and effective against new threats.
CIS also manages the U.S. Multi-State Information Sharing and Analysis Center (MS-ISAC). This program delivers threat intelligence and incident response to SLTT governments. For instance, local and state agencies in Florida—including Miami—receive alerts and cybersecurity guidance through MS-ISAC. This shows how vital CIS is in the U.S. cybersecurity ecosystem.
CIS receives funding from membership fees, product and services sales, and government grants. Its growth over the past two decades – now with over 500 employees – reflects the rising importance of its mission in an era of constant cyber threats.
In summary, CIS is the organization behind some of the world’s most widely used cybersecurity best practices. Next, we explore those practices in detail, starting with the CIS Controls.

CIS Critical Security Controls: 18 best practices for cyber defense
The CIS Critical Security Controls (often called CIS Controls) are a set of actionable cybersecurity best practices. They help organizations focus on the most important defensive measures first.
Originally developed by the SANS Institute as the “Top 20 Critical Security Controls,” they are now managed by CIS. The framework has evolved into 18 controls (as of Version 8) that cover a wide range of security areas.
Each CIS Control represents a broad security topic, such as asset inventory, access control, or malware defense. Inside each control, there are specific Safeguards (previously called sub-controls). These offer clear, step-by-step instructions to implement the control.
The CIS Controls are created and maintained by a global community of cybersecurity experts. This ensures they stay relevant and respond to real-world threats.
In Version 8, the controls were updated to reflect modern needs like cloud and mobile environments. They are now organized by activity, not by who manages the asset.
Key features of CIS controls:
Prioritized Implementation Groups (IGs): To help organizations of different sizes and risk levels, CIS v8 defines three Implementation Groups.
IG1 is basic cyber hygiene – a minimum standard of security that every enterprise should implement first. IG1 covers a subset (56) of the Safeguards, primarily the essentials that defend against the most common attacks.
IG2 and IG3 add more Safeguards for organizations with more resources or higher risk, building on the IG1 foundation. This tiered approach ensures that even smaller organizations (such as a small business in Miami with limited IT staff) know where to start (IG1) and can progressively harden their security as they grow. In fact, just implementing IG1 (which includes 15 of the 18 Controls) can protect against around 85% of common cyber attacks according to CIS analysis.
Actionable and Specific:
The Controls are very explicit about “what to do” – for example, CIS Control 1 is Inventory and Control of Enterprise Assets (keep track of all devices), and it includes Safeguards like “utilize an active discovery tool to identify devices connected to the network”.
This level of detail provides a clear roadmap. The CIS Controls serve as a “framework of frameworks,” distilling the most important elements from other standards (like NIST, ISO, etc.) into a focused set of actions. In other words, while broad frameworks might outline a comprehensive program, CIS Controls tell you how to execute security improvements in practical steps.
The 18 CIS Critical Security Controls cover areas such as inventory of hardware and software, data protection, secure configuration, continuous vulnerability management, audit log management, email and web defenses, malware protection, incident response, penetration testing, and more. This comprehensive coverage means the framework touches all aspects of an organization’s attack surface.
Importantly, the CIS Controls are technology-agnostic; they focus on outcomes rather than specific vendor solutions. For example, a control might urge you to implement multi-factor authentication or encrypt data, but it doesn’t dictate which product to use – you choose what fits your environment. This makes the Controls widely applicable, whether you run a small on-premises network or a large cloud infrastructure.
How CIS Controls help:
By implementing the CIS Controls, organizations significantly strengthen their defenses against common threats. CIS’s Community Defense Model v2.0 found that the Controls (especially IG1) mitigate the tactics used in the top five prevalent attack types (more on that in the CDM section below). In plain terms, if you follow the CIS Controls, you’re covering your bases against the kinds of attacks that are hitting organizations every day – from ransomware to data breaches. It’s a prescriptive to-do list for cybersecurity.
Video: how CIS critical security controls can help you
For a visual overview, check out the official CIS video “How CIS Critical Security Controls Can Help You” on YouTube. This short video illustrates how implementing the CIS Controls can protect your organization and why prioritizing security measures is so important. Watch it here: How CIS Critical Security Controls Can Help You.
(In the video, you’ll learn how the CIS Controls provide a security roadmap for businesses of all sizes – a great resource if you’re introducing these concepts to your team.)
CIS Benchmarks: Secure configuration standards for systems and software
The CIS Controls help organizations know what security activities to prioritize. Meanwhile, the CIS Benchmarks offer detailed guidance on how to configure systems securely.
These benchmarks are security hardening guides based on expert consensus. They define secure configuration standards for operating systems, cloud platforms, applications, and more.
By applying CIS Benchmarks, organizations can set up their systems and software in the most secure way. This reduces vulnerabilities and helps defend against cyber attacks.
What are CIS Benchmarks?
There are over 100 CIS Benchmark documents and tools. Each one recommends secure settings for different technologies.
These benchmarks are created through a consensus process. Experts from academia, industry, and government all contribute to them.
CIS Benchmarks are unique. They are the only configuration guides developed and accepted by a truly global cybersecurity community.
The concept is simple. A group of experts agrees on what a good security configuration looks like for platforms like Windows 11, AWS, or Oracle Database. That agreement becomes the baseline recommendation.
How are CIS Benchmarks structured?
Each CIS Benchmark works like a checklist of settings.
For example, a Windows Server benchmark includes rules for password policies, audit logging, and user account settings. It also covers services that should be disabled, firewall rules, registry values, and more. All settings aim to improve security without breaking functionality.
Every recommended setting includes two elements: a rationale (why it matters) and an impact (what might change). This helps IT administrators make informed decisions.
CIS Benchmarks often have different levels.
Level 2 offers stronger protection but may be more restrictive.
Level 1 focuses on essential security with minimal impact on usability.
Scope and coverage:
CIS Benchmarks cover over 25 vendor product families across all major domains of technology. This includes:
Operating Systems
Windows, Linux (multiple distributions like Ubuntu, Red Hat, etc.), macOS, Solaris, AIX, etc.
Server Software
Web servers (Apache, Nginx, IIS), databases (SQL Server, MySQL, Oracle DB, PostgreSQL, MongoDB), email servers, DNS servers (BIND), etc.
Cloud and Cloud Services
Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform, Oracle Cloud, IBM Cloud, and even specific services within those (like AWS S3, Kubernetes, Docker containers, etc.).
Network Devices
Routers, firewalls, VPN appliances from vendors like Cisco, Juniper, Palo Alto, etc.
Applications and Middleware
Web browsers (Chrome, Firefox, Safari, Edge), office suites, virtualization platforms (VMware), mobile device settings (Android, iOS), and so on.
In short, if your organization uses it, chances are there’s a CIS Benchmark for it. As of early 2025, there are 100+ CIS Benchmarks spanning dozens of technologies, and new ones are added as technology evolves (for example, Benchmarks for Kubernetes security, cloud services, and even things like Zoom have been released in recent years).
Why CIS Benchmarks matter:
Default configurations of systems are often not very secure. Vendors typically prioritize ease of use and compatibility over security out-of-the-box. This can leave unnecessary services enabled, weak settings, or default accounts that attackers can exploit. CIS Benchmarks provide a trusted blueprint to harden these systems – essentially, to turn off the unnecessary features and tune up the security knobs. Adhering to these benchmarks can dramatically reduce vulnerabilities. For instance, something as simple as disabling unused ports and accounts, or enforcing strong encryption protocols, can thwart many automated attacks.
CIS Benchmarks are widely used as secure configuration standards. Many regulatory and compliance frameworks rely on them.
Organizations pursuing certifications like ISO 27001 often use CIS Benchmarks. They help meet requirements for secure configuration.
The benchmarks are also mapped to frameworks like NIST SP 800-53. This makes them useful for audits and cybersecurity programs.
Some U.S. federal agencies and contractors rely on CIS Benchmarks. Others use the DISA STIGs, which are similar guides. Both help meet federal security mandates.
One great aspect: CIS Benchmarks are available for free in PDF format for anyone to download and use (for non-commercial purposes). This allows even small organizations to benefit from them without cost. For commercial use or if you want more automated usage of the benchmarks (like content in SCAP format, etc.), CIS offers that through its SecureSuite membership (more on that next).
To give a flavor, here are a few example recommendations one might find in various CIS Benchmarks:

Windows Server Benchmark example:
“Ensure Password History is set to 24 or more passwords” – this prevents users from reusing old passwords too quickly (a simple setting that improves password security).
AWS Benchmark example:
“Ensure multi-factor authentication (MFA) is enabled for all IAM users with console access” – a critical cloud security step.
Linux Benchmark example:
“Disable X Window System (GUI) on servers” – if you don’t need a GUI on a Linux server, don’t install it, to reduce attack surface.
Oracle Database Benchmark example:
“Ensure the ‘SYS’ and ‘SYSTEM’ default accounts have strong, non-default passwords.”
Applying CIS Benchmarks can be done manually (following the PDF checklist) or automated with tools. Many organizations integrate these recommendations into their system build process or use scripts and tools to enforce them. The result is a system configured in line with industry best practices, significantly lowering the risk of compromise.
In summary, CIS Benchmarks are secure configuration guides developed through global consensus. They help you lock down your systems and software.
By applying them, any organization—even in places like Miami—can align its IT environment with global security standards. This helps close common security gaps that attackers often target.
CIS Benchmarks work perfectly with the CIS Controls. While the Controls tell you what to focus on, the Benchmarks explain how to apply secure settings to your systems.
CIS SecureSuite Membership: Tools to implement CIS benchmarks and controls
Implementing dozens of CIS Benchmarks and continually measuring yourself against the CIS Controls can be a lot of work. To help with this, the Center for Internet Security offers a paid membership program called CIS SecureSuite®. A CIS SecureSuite Membership provides organizations with integrated cybersecurity tools and resources that make it easier to adopt the CIS Benchmarks and CIS Controls.
What does CIS SecureSuite include? At its core, membership gives you access to advanced tools, content, and support for CIS benchmarks and controls. Key benefits of CIS SecureSuite Membership include:
CIS-CAT pro assessment tool:
Members get access to CIS-CAT Pro, a powerful configuration assessment and auditing tool. CIS-CAT Pro can scan your systems (servers, workstations, etc.) and automatically compare their settings to the CIS Benchmarks. It then reports which settings are compliant and which are not, along with remediation guidance. This saves hours of manual checking. The tool supports assessing conformance to 100+ CIS Benchmarks in an automated way. Essentially, CIS-CAT Pro tells you how “hardened” your systems are according to CIS’s standards, and tracks your compliance over time via dashboards.
Enhanced CIS Benchmark content:
While anyone can download PDFs of the benchmarks, SecureSuite members can download benchmarks in machine-readable formats (like XML, Excel, etc.) and leverage CIS Build Kits. Build Kits are scripts and files (for Windows Group Policy, for example) that apply CIS Benchmark settings automatically. This is a huge time-saver for system administrators. For instance, instead of manually configuring each setting on a Windows server, you could apply a Group Policy template from CIS that implements the Benchmark recommendations. Members also get the latest benchmarks immediately upon release and can use them internally or in products with proper licensing. (This is useful for cybersecurity product vendors who want to embed CIS Benchmark guidance in their tools.)
CIS Controls tools:
SecureSuite membership also helps with the Center for Internet Security Controls implementation. Members have access to the Center for Internet Security Controls Assessment Specification and CIS CSAT (CIS Controls Self Assessment Tool). CIS CSAT is a web application that lets you track your progress on implementing the CIS Controls, assign tasks, and measure maturity over time – great for project management of a security program. Additionally, membership provides mappings and guides that show how CIS Controls map to other frameworks, which can simplify compliance reporting.
Community and Support:
CIS SecureSuite members get access to extra support. They can ask questions about benchmarks or controls.
Members also receive exclusive content, including webinars and implementation guides. The WorkBench forum allows them to collaborate, share ideas, and get help from other professionals.
According to CIS, SecureSuite is scalable and flexible. It adapts to the needs of any organization—small businesses or large enterprises. The tools help assess, automate, and improve your cybersecurity practices.
For example, a tech company in Miami with 50 servers could use CIS-CAT Pro. This tool allows them to run weekly compliance scans and keep their servers aligned with CIS Benchmarks.
At the same time, their security team could use Center for Internet Security CSAT. It helps them track progress on CIS Controls such as asset management or incident response.
It’s worth noting that membership is free for U.S. State, Local, Tribal, and Territorial governments (as part of CIS’s mission to support public sector cybersecurity). For others, it’s a paid annual subscription, with pricing tiers based on organization size/type. Many organizations find value in membership because it reduces the manpower needed to audit and maintain security baselines.
In summary, CIS SecureSuite Membership equips you with practical tools to operationalize CIS Benchmarks and Controls. Instead of doing everything manually, members can automate configuration checks with CIS-CAT Pro, quickly harden systems with build kits, and track their security improvements over time. This can accelerate your journey toward a secure environment and make ongoing compliance much easier.
CIS Community Defense Model (CDM) 2.0: Measuring the effectiveness of CIS controls
One question many organizations ask is: if we implement all these CIS Controls and Benchmarks, what threats will that actually stop?
The CIS Community Defense Model (CDM) was created to answer that. The CIS Community Defense Model 2.0 is an official white paper and framework (published in September 2021) that analyzes how well the CIS Critical Security Controls defend against the most common cyber-attacks organizations face.
In essence, CDM v2.0 takes real-world threat data – drawn from sources like threat reports and the MITRE ATT&CK framework – and uses it to validate the value of the CIS Controls. It asks: Which attacks are the most prevalent, and would implementing the CIS Controls stop those attacks? The analysis then guides defenders on how to prioritize security investments.
Key insights from CIS community defense model v2.0:
Focus on top five attack types:
The model identified the top five most prevalent attack types affecting enterprises, based on industry threat data. These are: Malware, Ransomware, Web Application Hacking, Insider and Privilege Misuse, and Targeted Intrusions. These five categories cover a large portion of the threat landscape – from opportunistic malware infections and ransomware outbreaks, to hacking of websites/applications, malicious insider actions, and sophisticated targeted attacks (often by advanced threat actors). Essentially, if you can defend against these five, you’re in a good position.
CIS controls effectiveness:
The CDM v2.0 found that the CIS Critical Security Controls offer strong protection. They defend well against the techniques used in the most common types of cyber attacks.
According to CIS, version 8 of the Controls blocks around 86% of those attack techniques. These are defined in the MITRE ATT&CK framework.
Even the basic Implementation Group 1 controls are highly effective. They provide a solid foundation to stop the majority of common attacks.
This finding is powerful. It shows that organizations with just the first set of CIS Controls can block most generic threats.
Use of MITRE ATT&CK:
The methodology leverages the MITRE ATT&CK matrix (a globally recognized model of adversary tactics and techniques). CIS mapped each of the top five attack types to the specific ATT&CK techniques involved. Then they mapped each CIS Safeguard to the ATT&CK techniques it stops. By doing this, they could quantify coverage. For example, a ransomware attack might involve techniques like phishing (initial access), disabling backups, encrypting data, etc. The CDM checks which CIS Controls/Safeguards would intercept those steps. The result: a measurable understanding of how the Controls thwart real attacks.
Findings and recommendations:
The Community Defense Model 2.0 confirmed that the CIS Controls offer excellent coverage. They help defend against top threats across the entire attack kill-chain.
The model also identified which CIS Safeguards are most effective across different attack types. One key finding was the value of secure configurations. This refers to applying CIS Benchmarks, which align with CIS Control 4 in version 8.
Secure configuration was called a “linchpin” Safeguard. It plays a critical role in defending against all kinds of cyber attacks.
Other high-value Safeguards include vulnerability management, data backups, and access control. These measures help reduce risk across multiple attack techniques.
Prioritization:
By understanding which controls mitigate multiple attack types, organizations can better prioritize implementation if they haven’t implemented all CIS Controls yet. The CDM v2.0 emphasizes starting with IG1 Safeguards (essential cyber hygiene) because they address the bulk of threats. It’s a data-driven confirmation that “doing the basics” (like inventory, patching, secure configuration, backups, monitoring logs) prevents the majority of incidents – which is encouraging for resource-strapped teams. Then, organizations facing more targeted or advanced threats can layer on IG2/IG3 Safeguards for additional protection.
In summary, the CIS Community Defense Model 2.0 is a valuable white paper (available from CIS) that essentially says: Yes, the CIS Controls work. It uses real-world data to show that following the CIS Controls can defend against common cyber attacks (malware, ransomware, web hacks, insider threats, etc.) with high effectiveness.
This gives organizations confidence that time and money spent implementing CIS’s best practices is well justified by the risk reduction. It also helps security leaders explain the importance of these measures to stakeholders (e.g., “By implementing these controls, we’re mitigating the majority of top threats as identified by industry research”).
For those interested, CIS Community Defense Model 2.0 can be downloaded for free from CIS’s website. It’s a highly recommended read for security professionals, as it bridges the gap between high-level frameworks and actual threat defense outcomes. It’s also a great example of how CIS continues to update its guidance – by validating and adjusting its Controls based on modern threats, ensuring that organizations focusing on CIS recommendations are focusing on what truly matters.
Implementing CIS benchmarks and controls in your organization (Miami, Florida and Beyond)
Knowing about CIS Benchmarks and Controls is one thing – implementing them effectively is another challenge. Many organizations, especially small and mid-sized businesses or those without large security teams, may find it daunting to assess their systems against CIS Benchmarks or to roll out all 18 CIS Controls. This is where partnering with experts can make a huge difference.
Ciegate Technologies is a strategic cybersecurity partner that can help companies put the CIS framework into practice. (Think of Ciegate as your local guide in Miami, Florida for navigating the CIS roadmaps to better security.) Leveraging a partner like Ciegate can provide several advantages:
Assessment and Gap Analysis:
Ciegate’s security consultants can perform a CIS Controls gap assessment to see where your current security posture stands relative to the CIS Controls. They identify which controls and safeguards you already have in place and which you’re missing.
Similarly, they can run CIS Benchmark compliance scans on your systems (using tools like CIS-CAT Pro or similar) to quickly pinpoint misconfigurations that need fixing. This gives you a clear, prioritized roadmap unique to your environment.
Expert Implementation Support:
With deep expertise in the Center for Internet Security guidelines, Ciegate can efficiently implement the needed security controls. For example, if your business needs to establish better audit logging (CIS Control 8) or improve network monitoring (Control 11), Ciegate can recommend and deploy the right tooling and processes.
If you need to harden servers according to CIS Benchmarks, Ciegate can assist in tweaking configurations or applying CIS Build Kits, and then validate that everything is set correctly. This kind of help is invaluable to avoid trial-and-error, ensuring you get security settings right the first time.
Policy Development and Training:
Implementing CIS Controls often involves developing policies (like an access control policy, incident response plan, etc.) and training staff (for security awareness per CIS Control 14).
Ciegate can help write these policies aligned to CIS recommendations and deliver training sessions to your IT team or general employees – for instance, training employees in Miami on best practices to avoid phishing (which ties into CIS Control 17 Security Awareness).
Ongoing Management and Compliance:
Cybersecurity isn’t a one-time project. Ciegate can provide managed services or periodic check-ins to ensure your organization maintains compliance with CIS Benchmarks and continues to mature in CIS Controls implementation. This might include scheduled scans, quarterly reviews, and updates to your program as new CIS versions or threat trends emerge. Essentially, they can help you institutionalize CIS best practices so that they become part of your regular IT operations.
Customization for Your Needs:
Every organization is different. A hospital in Florida will have different priorities than a tech startup or a financial firm. Ciegate Technologies brings experience across industries, so they can tailor the CIS framework to your specific regulatory needs (HIPAA, PCI, etc.), integrating it with other frameworks you might use (for example, if you also follow NIST or ISO standards). They can also highlight quick wins that make sense for your business’s size and risk profile, ensuring that improvements are impactful and cost-effective.
From a local perspective, having a partner familiar with the Miami, Florida business environment is a plus. Ciegate understands the regional threat landscape (for instance, trends in cyber threats targeting South Florida businesses or municipalities) and can respond quickly on-site if needed. They also offer the peace of mind that comes with knowing you have a dedicated team watching over your cybersecurity, so you can focus on running your business.
Lightly persuasive CTA: Every day, cyber attacks continue to grow in sophistication. Implementing CIS Controls and Benchmarks can dramatically reduce your risk, but you don’t have to do it alone. Ciegate Technologies can be your ally in this journey – helping translate CIS’s global best practices into a practical, effective security program for your organization. Whether you’re just starting to address cybersecurity or looking to strengthen an already mature system, consider reaching out to Ciegate for a consultation. With the right expertise by your side, aligning with the Center for Internet Security standards becomes not only achievable but efficient and smoothly integrated with your business goals.
Next Step: Ready to bolster your cybersecurity defenses with CIS best practices?
Contact Ciegate Technologies to learn how we can help you implement CIS Benchmarks and Critical Controls tailored to your organization’s needs. Together, we can turn the CIS guidance into concrete actions that protect your data, your customers, and your peace of mind.
Frequently Asked Questions about the Center for Internet Security (CIS)

Who funds the Center for Internet Security?
A: CIS is funded through a mix of sources. A significant portion comes from the sales of its cybersecurity tools and services – for example, organizations pay for CIS Secure Suite memberships (to get CIS-CAT Pro and other tools) and for CIS Hardened Images (pre-secured virtual machine images).
These direct product/service revenues help sustain CIS’s operations. Additionally, CIS receives grants and funding from government programs and contracts. In particular, the U.S. federal government (through agencies like the Department of Homeland Security/CISA) provides funding to support CIS’s role in operating the Multi-State ISAC for state and local governments.
CIS often operates certain initiatives on a cost-sharing model between its own funds and federal funds. Being a nonprofit, Center for Internet Security also occasionally gets support from philanthropic grants dedicated to improving cybersecurity. To summarize, CIS’s funding comes from membership fees, product sales, and government grants, all reinvested into its mission of making cyberspace safer.

What is the purpose of the Center for Internet Security?
The purpose of CIS is encapsulated in its mission: to make the connected world a safer place by developing and promoting best practice solutions to mitigate cyber threats.
In practical terms, CIS exists to identify what security measures work effectively against real-world threats and to guide organizations in implementing those measures. The CIS founders realized that all organizations – not just big enterprises – needed clear, actionable advice to defend against hackers.
Therefore, CIS’s role is to gather the expertise of the cybersecurity community and create standards, tools, and services that anyone can use to improve their security posture.
The CIS Critical Security Controls and CIS Benchmarks are the prime examples of this purpose in action: they are distilled “best practices” that help organizations focus on the most important security steps. Overall, the purpose of CIS is to help people, businesses, and governments protect themselves against pervasive cyber threats by providing practical, accessible cybersecurity guidance.
What is the difference between CIS and NIST?
Both CIS and NIST are key players in cybersecurity standards, but they have different origins and focus areas, and they often complement each other. Here are a few differences:
Organization Type:
CIS is an independent nonprofit organization, whereas NIST (National Institute of Standards and Technology) is a U.S. government agency (part of the Department of Commerce). This means NIST’s frameworks (like NIST Cybersecurity Framework, NIST 800-53, etc.) are government-published and often tied to federal compliance, while CIS’s guidance is community-driven and voluntary.
Scope and Purpose:
NIST produces very comprehensive standards and frameworks that cover a wide range of cybersecurity and risk management topics. For example, NIST SP 800-53 is a large catalog of hundreds of security controls for federal information systems, and the NIST Cybersecurity Framework is a high-level framework for managing cyber risk (identify, protect, detect, respond, recover).
These are often used as overall policy frameworks or for compliance mandates (indeed, U.S. federal agencies must follow NIST standards, and many contractors and critical infrastructure firms adopt them too). CIS, on the other hand, focuses on practical implementation and prioritization.
The CIS Controls are more prescriptive and prioritized – a lean list of 18 control domains with specific Safeguards to implement. They are designed to be actionable step-by-step best practices. In short, NIST often tells you what a robust security program should encompass, while CIS tells you which parts to do first and how to do them in detail. For example, NIST might require you to have an access control policy; CIS will provide specific guidance like “inventory all accounts, implement MFA, etc.”
Level of Detail:
NIST guidelines (like 800-53 or 800-171) can be very exhaustive and somewhat abstract, meant to cover all bases. CIS guidelines (Controls and Benchmarks) are typically more focused and technically detailed for implementation. For instance, NIST CSF says “protect your data,” while CIS Controls break that into specific safeguards like encrypt data at rest, manage encryption keys, etc. CIS Benchmarks go even deeper by giving exact configuration settings. One could say Center for Internet Security content is more prescriptive (do X, Y, Z specifically), whereas NIST is more descriptive (ensure you address these categories of risk).
In summary, NIST provides broad, comprehensive security frameworks (often required for compliance), while CIS provides distilled, prioritized best practices for actual implementation.
They are not competitors; rather, CIS builds on and complements frameworks like NIST. A popular saying is: Use NIST to define the “what” and CIS to guide the “how.” If you’re a company in Miami, for instance, with no regulatory obligations, you might jump straight to CIS Controls to secure yourself. If you’re aiming for a federal contract or a mature enterprise program, you might align with NIST CSF and use CIS Controls/Benchmarks as the implementation baseline within that framework.
How many employees does the Center for Internet Security have?
CIS has grown significantly over the years. As of 2025, the Center for Internet Security has around 500 employees. A news article in April 2025 noted that CIS’s staff size was 506, which was a 6% increase from the previous year. These employees include cybersecurity experts, engineers, analysts, and support staff who work on developing the Center for Internet Security Benchmarks and Controls, running the MS-ISAC and EI-ISAC (for state and election security), and providing services to members.
The workforce is distributed with headquarters in New York and some presence in Washington, D.C., and many staff working remotely across the country. The growth in staff reflects CIS’s expanding role in areas like critical infrastructure security and the demand for its guidance. For context, a decade ago CIS was much smaller; its expansion to ~500 employees shows how cybersecurity has become a priority area necessitating more personnel. Despite this growth, Center for Internet Security relies heavily on community volunteers and experts (outside of these employees) who contribute their time to developing benchmarks and controls. So the extended “CIS family” of contributors is even larger.
How does CIS make money?
Since CIS is a nonprofit, it doesn’t exist to make profits, but it still needs revenue to operate and fund its mission. CIS earns money in a few primary ways:
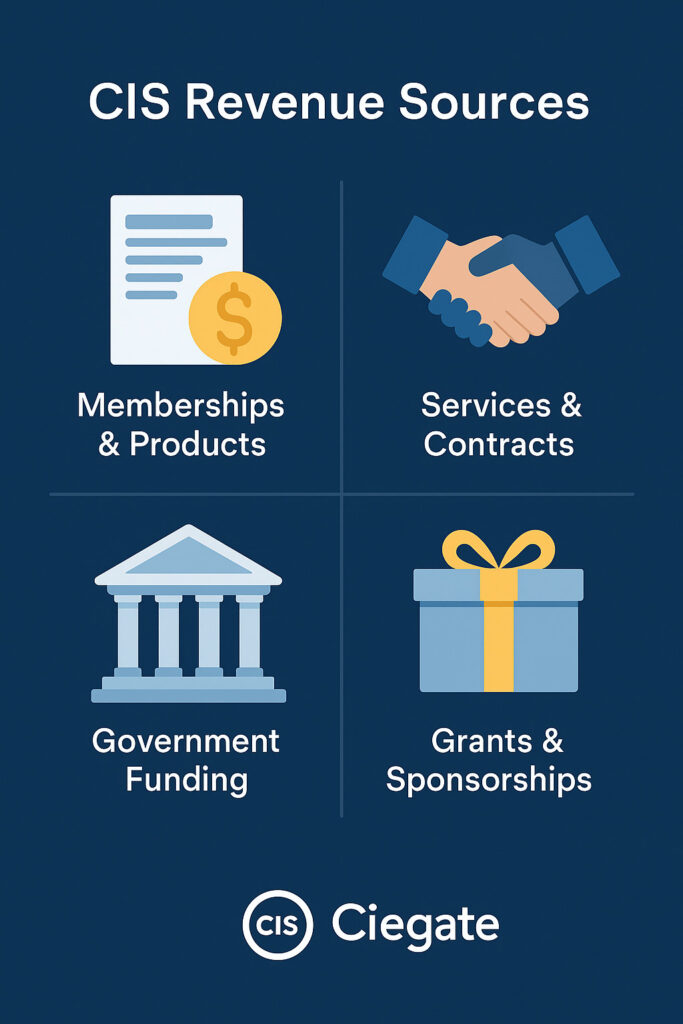
Memberships and Products:
The CIS SecureSuite Membership is a paid subscription that organizations worldwide purchase to get access to CIS-CAT Pro and other tools. By offering tiered memberships to businesses, consulting firms, and product vendors, CIS generates revenue.
Similarly, CIS offers CIS Hardened Images (virtual machine images for cloud platforms that come pre-secured to CIS Benchmark standards) on cloud marketplaces – these are sold for a fee. Each time a company uses a CIS Hardened Image (say an AWS AMI that is CIS-hardened), CIS gets a portion of that fee. These product sales are a key income stream.
Services and Contracts:
CIS, through the MS-ISAC, provides certain cybersecurity services (like Albert network monitoring sensors for governments, or malicious domain blocking services). Some of these are funded by contracts or cost-sharing agreements. For example, a state government might contract with CIS to roll out Albert intrusion detection sensors in all its counties – partially funded by a federal grant and partially by the state. CIS might also receive payments for specialized training workshops or security assessments for members (though much of its training is free, some advanced or customized support might come with a fee).
Government Funding:
A chunk of CIS’s funding comes from U.S. federal support, especially for its work benefiting the public sector. The Department of Homeland Security (through CISA) provides grants to CIS to run the MS-ISAC and EI-ISAC as national resources. Congress appropriates funds for these via cooperative agreements. For instance, CIS’s MS-ISAC operations have historically been funded by federal grants to ensure all U.S. state and local governments can get cyber threat intelligence and help at no cost to them. Recent news indicates CIS is navigating adjustments in federal funding (as government budgets fluctuate), but it continues to receive support due to the critical nature of its services.
Grants and Sponsorships:
Occasionally, CIS may receive grants from foundations or sponsorship from organizations for specific initiatives (like improving election security or developing new benchmarks). However, by and large, CIS “makes money” by providing value-added cybersecurity resources (tools, content, support) to organizations that choose to pay for membership or services, and through public funding to carry out its nonprofit mission.
How organizations can benefit from Center for Internet Security: Free resources, reinvestment, and real-world impact
It’s important to note that many Center for Internet Security resources are free. Anyone can download the CIS Benchmarks or review the Controls without paying. These basic offerings are available to the entire community. Center for Internet Security generates revenue through premium features. These include automated tools, tailored support, and turn-key solutions. These paid services help fund CIS’s operations.
Unlike a for-profit company, Center for Internet Security reinvests any surplus. This supports the development of new frameworks, tools, and services for high-need areas.
When organizations understand CIS’s mission and resources, they can apply them more effectively. From funding to tools like CIS Controls and Benchmarks, everything is designed to strengthen cybersecurity.
Whether you need to secure your company’s systems or stop modern threats, Center for Internet Security offers proven best practices. Even businesses in places like Miami can implement strong defenses with CIS’s help.
With expert partners and free guidance available, any organization can follow world-class standards. In a world of evolving cyber threats, CIS’s community-driven approach provides clarity and confidence to those looking to protect their digital assets.
Ciegate Technologies Miami
📍Address: 8950 SW 74th Court, Suite 2201, Miami, FL 33156
📞Phone: 305-501-2880
Google Profile: Ciegate Miami
View on Map
Ciegate Technologies Charlotte
📍Address: 615 S College St, Floor 9, Charlotte, NC 28202
📞Phone: 704-498-8198
Google Profile: Ciegate Charlotte
View on Map
Related terms: CIS, center for internet security, center for internet security inc, cis center for internet security